Everything posted by ResidentialBusiness
-
HP Launches Smart Retail Solutions to Enhance Unified Commerce
In a bold move set to transform the retail landscape, HP Inc. has launched its Intelligent Retail Solutions, marking a significant advancement in unified commerce. Aimed at empowering retailers, these solutions merge hardware, software, and intelligent services, offering businesses greater control, consistency, and visibility in their operations. This initiative comes at a crucial time for small businesses navigating a post-pandemic retail environment, where customer expectations are evolving rapidly. Retailers face a myriad of challenges, from inventory management to customer engagement. HP’s new offerings could be the game-changing resources they need. “Our Intelligent Retail Solutions illuminate the path forward for retailers as they embrace a dynamic landscape that demands flexibility and resilience,” said an HP spokesperson. This sentiment reflects a broader understanding that small businesses require innovative tools to effectively compete. One of the standout features of these retail solutions is their ability to integrate seamlessly into existing systems. For small business owners not equipped to invest heavily in new infrastructure, this feature is particularly advantageous. As inventory management becomes increasingly complex, having a solution that can bridge various systems—such as online and brick-and-mortar operations—will likely create a smoother experience for both staff and consumers. The integration also allows for enhanced data analysis, which is crucial for making informed business decisions. With real-time analytics, retailers can better manage stock levels, forecast trends, and tailor their marketing efforts. This data-driven approach can ultimately lead to increased customer satisfaction and, hence, higher sales—vital for small businesses aiming to grow. Moreover, HP is focusing on sustainability, another key interest area for modern consumers. Their solutions incorporate environmentally friendly practices which can enhance a brand’s reputation. Small businesses can leverage this aspect to connect more deeply with eco-conscious consumers, thus positioning themselves competitively in the marketplace. However, while the benefits are undeniable, small business owners should also consider potential challenges. Implementing new technology can be daunting—especially for businesses with limited resources and expertise. There may be a learning curve associated with the transition to these advanced systems, which could initially disrupt existing workflows. Additionally, while the prospect of enhanced inventory management and customer engagement is appealing, the upfront costs associated with these new systems could be a barrier for smaller retailers. It’s essential for business owners to weigh these costs against the potential for increased efficiency and sales. HP has positioned itself as a partner in this journey, offering support through training and resources to ease the transition. Small business owners should take advantage of these offerings to ensure they fully utilize the capabilities of the Intelligent Retail Solutions. As retailers continue to evolve, embracing technology will become not just advantageous but essential. HP’s Intelligent Retail Solutions offer a compelling opportunity for small businesses to adapt and thrive in an increasingly competitive landscape. For those looking to get ahead, this innovation could be the key to maintaining relevance and driving growth in an ever-changing economic environment. For more information on HP’s Intelligent Retail Solutions, visit the original press release here. Image via Google Gemini This article, "HP Launches Smart Retail Solutions to Enhance Unified Commerce" was first published on Small Business Trends View the full article
-
YouTube Expands Monetization For Some Controversial Issues via @sejournal, @MattGSouthern
YouTube is updating advertiser-friendly guidelines so some non-graphic videos on "controversial issues" may be eligible for full monetization. The post YouTube Expands Monetization For Some Controversial Issues appeared first on Search Engine Journal. View the full article
-
Skipping this exercise at the gym could be bad for your brain
“Never skip leg day” sounds like something a swole gym bro with killer quads might harp on about. But doctors also sing the praises of lunges and split bench squats, and not for the reason you might think. In a recent article for Vogue, California-based physician Dr. Chris Renna said: “Stronger leg muscles are linked to better cognitive function in aging mainly through their effects on blood flow, metabolic health, brain structure, and physical/social activity patterns.” Muscle mass starts to decline at age 30. As the largest muscle group in the body, maintaining muscle strength in the thighs and glutes is especially important for healthy aging—and apparently, brain function. Multiple studies back this up. A 2015 study of over 300 female twins, ages 43 to 73, found the more powerful their legs (measured by pushing one foot as hard and fast as possible against a pedal), the better their cognition a decade on (measured by a series of tests on memory and processing speed). Another study of 1,500 older adults, with an average age of 70, conducted in 2018, also found an association between stronger legs and better performance on tests of their cognitive function. A separate study also in 2018, this time conducted on mice, found exercising the lower extremities to be critical to brain and nervous system health. Researchers discovered that neurological health depends as much on signals sent from the leg muscles to the brain as it does the other way around. This offers an explanation for why patients with neurological diseases experience rapid decline once their movement becomes limited. “It is no accident that we are meant to be active: to walk, run, crouch to sit, and use our leg muscles to lift things,” the study’s author, Dr. Raffaella Adami, told academic journals publisher Frontiers. “Neurological health is not a one-way street with the brain telling the muscles ‘lift,’ ‘walk,’ and so on.” The brain-leg connection can be explained by tiny proteins called myokines. When the leg muscles are exercised, they release these messenger molecules, which reach the brain via the bloodstream. Here, they support learning ability, memory, and neural adaptation, the process by which the nervous system adjusts and improves its functioning. A simple leg day session that includes weight-bearing exercises like lunges, squats, and calf raises will not only improve physical strength. By increasing blood flow, the brain floods with extra oxygen, helping to decrease harmful inflammation in the body. If you’ve been known to skip squats or lunges at the gym, it doesn’t help that modern life is, for many, characterized by a concerning lack of movement. Commuting to work to sit at a desk for hours, before commuting home again to sit some more on the couch, means our legs often aren’t getting the regular exercise they need to keep our brain working optimally. So drop some squats in front of some Netflix or while listening to a podcast. Your glutes won’t be the only part of your body that thanks you. View the full article
-
Google Trends adds Gemini to Explorer page
Google is rolling out a new update for the Trends Explorer page that is powered by Gemini. The goal is to make it easier for users and researchers to find more search terms to explore. “The updated Explore page has a new side panel that uses Gemini capabilities to automatically identify and compare relevant trends for your area of interest,” Google wrote. What it looks like. There is this new layout and new “Suggest search terms” button at the top right of the page. Here is a screenshot: When you click on “Suggest search terms,” you can enter in a keyword or a natural language sentence and Gemini will help you break out all the terms and compare them to each other. Google will automatically identify and compare relevant trends for your area of interest, and provide a list of suggested Gemini prompts to help you explore further. Here is an example: Plus, Google rolled out a new, modern look to help you better understand trends data. “Each search term gets dedicated icons and colors, which makes it easier to match each term with its line on the graph. We’ve also increased the number of terms you can compare, and we’ve doubled the amount of rising queries we show on each timeline, so you can better understand why a query is trending,” Google added. Here is the old design: Gradual rollout. While I can see this new Google Trends explorer page today, some might not see it yet. Google said this is a gradual rollout on desktop right now. Why we care. This may give you new ways to explore fresh and new content ideas for your site. Give it a try, it might surprise you. View the full article
-
Sixteen Marketing Activities to Try
Maybe you can help a client at the same time. By August Aquila MAX: Maximize Productivity, Profitability and Client Retention Go PRO for members-only access to more August J. Aquila. View the full article
-
Sixteen Marketing Activities to Try
Maybe you can help a client at the same time. By August Aquila MAX: Maximize Productivity, Profitability and Client Retention Go PRO for members-only access to more August J. Aquila. View the full article
-
Mortgage rates slide to one of lowest levels since 2022
The contract rate on a 30-year mortgage dropped 7 basis points to 6.18% in the week ended Jan. 9, according to Mortgage Bankers Association data released Wednesday. View the full article
-
Personal Intelligence with Gemini connect your searches, email, photos, and YouTube history
Google has introduced “Personal Intelligence” in the Gemini app as a beta which allows Gemini to give you a more personalized response by connecting across your Google ecosystem, including Google Search, Gmail, Photos, and your YouTube history. Google said this is “Launching as a beta in the U.S., this marks our next step toward making Gemini more personal, proactive and powerful.” This will also be coming to Search in AI Mode soon, Google told us. While Gemini could already retrieve information from these apps, with Gemini 3, it can now reason across your data to surface proactive insights. Here is how it looks. Here is a video of how it works: Availability. This feature is rolling out today to some Google users: Rolling out over the course of the day—14th January—to Google AI Pro and AI Ultra subscribers in the U.S. It should reach all eligible users within the week. Once enabled, it works across Web, Android and iOS and with all of the models in the Gemini model picker. Google will soon expand to more countries and the free tier. It’s also coming to Search in AI Mode soon. This is right now only available for personal Google accounts and not for Workspace business, enterprise or education users. Privacy, control and personalization. Here are some of the privacy controls and personalization settings: This experience is off by default, so you can decide if and when to connect apps to Gemini. Even when your apps are connected, Google won’t personalise every response. You can also connect some apps without connecting others To keep making your conversations helpful, Gemini will continue personalising your experience by referencing your past chats by default. You can stop this by turning off the setting called your “Past Gemini chats.” You can also manage and delete your past chats anytime. You can decide not to personalise certain responses via the try again button Give feedback about personalisation via thumbs down button Why we care. This is coming to AI Mode in Google Search, and this may play a role in your track visibility in these tools. If much of the experience is super personalized, then tracking AI results will be really challenging. View the full article
-
China’s trade surplus soared to a record $1.2 trillion in 2025, despite Trump’s tariffs
China’s trade surplus surged to a record of almost $1.2 trillion in 2025, the government said Wednesday, as exports to other countries made up for slowing shipments to the U.S. under President Donald The President’s onslaught of higher tariffs. China’s exports rose 5.5% for the whole of last year to $3.77 trillion, customs data showed, as Chinese automakers and other manufacturers expanded into markets across the globe. Imports flatlined at $2.58 trillion. The 2024 trade surplus was over $992 billion. In December, China’s exports climbed 6.6% from the year before in dollar terms, better than economists’ estimates and higher than November’s 5.9% year-on-year increase. Imports in December were up 5.7% year-on-year, compared to November’s 1.9%. China’s trade surplus surpassed the $1 trillion mark for the first time in November, when the trade surplus reached $1.08 trillion in the first 11 months of last year. Economists expect exports will continue to support China’s economy this year, despite trade friction and geopolitical tensions. “We continue to expect exports to act as a big growth driver in 2026,” said Jacqueline Rong, chief China economist at BNP Paribas. While China’s exports to the U.S. fell sharply after The President returned to office and escalated his trade war with the world’s second-largest economy, that decline has been largely offset by shipments to other markets in South America, Southeast Asia, Africa and Europe. For the whole of 2025, China’s exports to the U.S. fell 20%. In contrast, exports to Africa surged 26%. Those to Southeast Asian countries jumped 13%; to the European Union 8%, and to Latin America, 7%. Strong global demand for computer chips and other devices and the materials needed to make them were among categories that supported China’s exports, analysts said. Exports of electronics and electrical equipment were by far the largest export category, rising 8.4% from a year earlier. Car exports also grew last year. Auto exports surged 21% in 2025 to more than 7 million units, driven by electric vehicles and plug-in hybrids, according to the China Association of Automobile Manufacturers, an industry group, on Wednesday. China also exported more grain and fertilizer, while its sales of furniture, shoes and other labor intensive products fell. Strong exports have helped keep China’s economy growing at an annual rate close to its official target of about 5%. That has triggered alarm in countries that fear a flood of cheap imports is damaging local industries. China faces a “severe and complex” external trade environment in 2026, Wang Jun, vice minister of China’s customs administration, told reporters in Beijing. But he said China’s “foreign trade fundamentals remain solid.” The head of the International Monetary Fund last month called for China to fix its economic imbalances and speed up its shift from reliance on exports by boosting domestic demand and investment. A prolonged property downturn in China after the authorities cracked down on excessive borrowing, triggering defaults by many developers, is still weighing on consumer confidence and domestic demand. China’s leaders have made increasing spending by consumers and businesses a focus of economic policy, but actions taken so far have had a limited impact. That included government trade-in subsidies over the past months that encouraged consumers to buy newer, more energy efficient items, such as home appliances and vehicles. “We expect domestic demand growth to stay tepid,” said Rong of BNP Paribas. “In fact, the policy boost to domestic demand looks weaker than last year — in particular the fiscal subsidy program for consumer goods.” In the case of autos, domestic sales rose 6% in 2025, but they fell back toward the end of the year as those subsidies were scaled back or phased out in some areas. Gary Ng, a senior economist at French investment bank Natixis, forecasts that China’s exports will grow about 3% in 2026, less than the 5.5% growth in 2025. With slow import growth, he expects China’s trade surplus to remain above $1 trillion this year. —Chan Ho-Him, AP Business Writer View the full article
-
US home resales climb to strongest pace since 2023
Contract closings rose 5.1% to a 4.35 million annualized pace last month, the highest since February 2023, according to figures released Wednesday by the National Association of Realtors. View the full article
-
What Is MySBA Loan Portal and How Can It Help Your Business?
The MySBA Loan Portal is a digital tool that can greatly improve your small business’s financial management. It offers a user-friendly dashboard to monitor your SBA 504 loans, allowing you to view outstanding balances and payment histories easily. With features like direct payments and messaging with SBA representatives, this portal streamlines your cash flow management. Interested in how these functionalities can particularly benefit your business operations? Key Takeaways MySBA Loan Portal is a web-based platform that centralizes the management of SBA 504 loans for small businesses. It features a user-friendly dashboard displaying loan balances, maturity dates, and payment history for easy monitoring. The portal allows direct payments for various SBA loans, streamlining cash flow management for businesses. Users can access IRS 1098 tax forms, simplifying tax preparation and documentation. The platform provides direct messaging with SBA representatives, ensuring efficient support and communication for loan inquiries. Overview of MySBA Loan Portal The MySBA Loan Portal serves as a thorough, web-based platform that enables borrowers to efficiently manage their SBA 504 loans. This centralized hub allows you to access crucial loan information and documents with ease. From the user-friendly dashboard, you can view key details like outstanding balances, maturity dates, loan amounts, and monthly payments, simplifying financial oversight. Furthermore, the portal provides access to your complete payment history and IRS 1098 tax forms, making record-keeping straightforward. New users can register by entering their SBA loan number and social security number, whereas existing users can use their credentials for secure mysba login. The MySBA Loan Portal likewise facilitates direct messaging with SBA representatives, ensuring you receive support for your loans and accounts when needed. Overall, this platform improves your ability to manage your SBA 504 loans efficiently, enhancing your financial management experience. Key Features and Benefits When you utilize the MySBA Loan Portal, you’ll discover a range of significant features and benefits aimed at improving your loan management experience. The portal offers a centralized dashboard where you can monitor all your SBA loans, including outstanding balances, payment history, and important details like maturity dates and monthly payments. You’ll additionally have easy access to vital loan information and IRS 1098 tax forms, which can improve your financial management capabilities. Furthermore, the portal enables direct payments for PPP loans, Economic Injury Disaster Loans (EIDL), and SBA 7(a) loans, streamlining the repayment process. You’ll receive automatic email notifications for new document uploads, keeping you informed about your loan status and important updates. With its user-friendly interface and messaging capabilities, you can efficiently manage your loans and communicate with SBA representatives whenever you need assistance. How to Access the Portal Accessing the MySBA Loan Portal is a straightforward process that allows you to manage your loans effectively. To get started, visit the link https://lending.sba.gov/. If you already have an account, simply log in using your existing MySBA credentials, which may include those from CAFS and Veteran Certification accounts. If you’re a new user, you’ll need to register for an account. During this process, be ready to provide your social security number and at least one SBA loan number. Once you’re registered, you’ll find the portal’s user-friendly interface helpful for maneuvering through your loan details. You can easily check your outstanding balances, review payment history, and make payments directly through the portal. This secure access guarantees you can manage your loans efficiently, keeping all necessary information at your fingertips. Customer Support and Resources Once you’ve logged into the MySBA Loan Portal, you might find yourself needing extra assistance or resources to better understand your loan details. Fortunately, the portal provides a customer service center where you can call 1-833-572-0502 for support inquiries related to your loan specifics and payment processes. Experienced loan experts are on hand to help you grasp loan terms and conditions, in addition to answering questions about more SBA 504 loans. You can likewise communicate directly with SBA representatives through the portal, allowing for timely assistance regarding your loans and accounts. If you encounter access issues or have general inquiries, reach out to SDC at (334) 244-1801 or via email for personalized support. Furthermore, stay informed through SDC spotlight features and road show events in Alabama, which share regular updates and resources to keep you engaged in your borrowing experience. Impact on Small Business Management The MySBA Loan Portal greatly impacts small business management by providing a centralized dashboard that simplifies the monitoring and management of SBA loans. You can easily track outstanding balances and payment histories, which helps you stay on top of your financial obligations. The portal’s user-friendly interface allows for informed decision-making, enabling you to assess your loan performance effortlessly. You can as well make payments directly through the portal, streamlining your cash flow management. Automatic email notifications for new document uploads keep you updated on important changes, allowing for proactive loan management. Furthermore, access to IRS 1098 tax forms simplifies your tax preparation, reducing the time spent on administrative tasks. This combination of features not only improves your ability to manage loans effectively but likewise contributes to better overall financial health for your business. Frequently Asked Questions What Is the Mysba Loan Portal? The MySBA Loan Portal is an online platform that simplifies your management of SBA loans. It features a dashboard where you can view important loan details, such as outstanding balances and payment history. You can easily sign in or create an account using your social security number and loan number. The portal additionally allows you to make payments, access statements, and communicate with SBA representatives, ensuring you stay organized and informed about your loans. How Do Loans Help Businesses? Loans help businesses by providing vital capital for various needs, like starting operations, broadening facilities, or purchasing equipment. They enable you to manage cash flow, ensuring you can meet operational costs during market fluctuations. Furthermore, securing a loan can improve your credit profile when payments are made on time, paving the way for better financing options later. Certain loan programs offer favorable terms, making long-term financing more accessible and affordable for small businesses like yours. What Is Mysba? MySBA is a digital platform created by the Small Business Administration, focusing on managing 504 loans. It offers a user-friendly dashboard where you can view all your loans, including outstanding balances and payment history. By logging in with your social security number and SBA loan number, you can access crucial documents like IRS 1098 tax forms. The portal likewise allows direct communication with the SBA, making it easier to address any loan-related inquiries. Can Someone Help Me With My SBA Loan Login? If you’re having trouble logging into your SBA loan account, you can reach out for help. First, verify you’re using the correct credentials. If you still can’t access your account, call the customer service center at 1-833-572-0502 for assistance. They can guide you through troubleshooting steps. Conclusion In conclusion, the MySBA Loan Portal offers a thorough solution for managing SBA 504 loans, providing crucial features like direct payments and easy access to loan information. By utilizing this platform, you can improve your business’s financial management and decision-making processes. Accessing the portal is straightforward, and ample customer support is available to assist you. Overall, integrating the MySBA Loan Portal into your operations can greatly enhance your efficiency and streamline your loan management tasks. Image via Google Gemini This article, "What Is MySBA Loan Portal and How Can It Help Your Business?" was first published on Small Business Trends View the full article
-
What Is MySBA Loan Portal and How Can It Help Your Business?
The MySBA Loan Portal is a digital tool that can greatly improve your small business’s financial management. It offers a user-friendly dashboard to monitor your SBA 504 loans, allowing you to view outstanding balances and payment histories easily. With features like direct payments and messaging with SBA representatives, this portal streamlines your cash flow management. Interested in how these functionalities can particularly benefit your business operations? Key Takeaways MySBA Loan Portal is a web-based platform that centralizes the management of SBA 504 loans for small businesses. It features a user-friendly dashboard displaying loan balances, maturity dates, and payment history for easy monitoring. The portal allows direct payments for various SBA loans, streamlining cash flow management for businesses. Users can access IRS 1098 tax forms, simplifying tax preparation and documentation. The platform provides direct messaging with SBA representatives, ensuring efficient support and communication for loan inquiries. Overview of MySBA Loan Portal The MySBA Loan Portal serves as a thorough, web-based platform that enables borrowers to efficiently manage their SBA 504 loans. This centralized hub allows you to access crucial loan information and documents with ease. From the user-friendly dashboard, you can view key details like outstanding balances, maturity dates, loan amounts, and monthly payments, simplifying financial oversight. Furthermore, the portal provides access to your complete payment history and IRS 1098 tax forms, making record-keeping straightforward. New users can register by entering their SBA loan number and social security number, whereas existing users can use their credentials for secure mysba login. The MySBA Loan Portal likewise facilitates direct messaging with SBA representatives, ensuring you receive support for your loans and accounts when needed. Overall, this platform improves your ability to manage your SBA 504 loans efficiently, enhancing your financial management experience. Key Features and Benefits When you utilize the MySBA Loan Portal, you’ll discover a range of significant features and benefits aimed at improving your loan management experience. The portal offers a centralized dashboard where you can monitor all your SBA loans, including outstanding balances, payment history, and important details like maturity dates and monthly payments. You’ll additionally have easy access to vital loan information and IRS 1098 tax forms, which can improve your financial management capabilities. Furthermore, the portal enables direct payments for PPP loans, Economic Injury Disaster Loans (EIDL), and SBA 7(a) loans, streamlining the repayment process. You’ll receive automatic email notifications for new document uploads, keeping you informed about your loan status and important updates. With its user-friendly interface and messaging capabilities, you can efficiently manage your loans and communicate with SBA representatives whenever you need assistance. How to Access the Portal Accessing the MySBA Loan Portal is a straightforward process that allows you to manage your loans effectively. To get started, visit the link https://lending.sba.gov/. If you already have an account, simply log in using your existing MySBA credentials, which may include those from CAFS and Veteran Certification accounts. If you’re a new user, you’ll need to register for an account. During this process, be ready to provide your social security number and at least one SBA loan number. Once you’re registered, you’ll find the portal’s user-friendly interface helpful for maneuvering through your loan details. You can easily check your outstanding balances, review payment history, and make payments directly through the portal. This secure access guarantees you can manage your loans efficiently, keeping all necessary information at your fingertips. Customer Support and Resources Once you’ve logged into the MySBA Loan Portal, you might find yourself needing extra assistance or resources to better understand your loan details. Fortunately, the portal provides a customer service center where you can call 1-833-572-0502 for support inquiries related to your loan specifics and payment processes. Experienced loan experts are on hand to help you grasp loan terms and conditions, in addition to answering questions about more SBA 504 loans. You can likewise communicate directly with SBA representatives through the portal, allowing for timely assistance regarding your loans and accounts. If you encounter access issues or have general inquiries, reach out to SDC at (334) 244-1801 or via email for personalized support. Furthermore, stay informed through SDC spotlight features and road show events in Alabama, which share regular updates and resources to keep you engaged in your borrowing experience. Impact on Small Business Management The MySBA Loan Portal greatly impacts small business management by providing a centralized dashboard that simplifies the monitoring and management of SBA loans. You can easily track outstanding balances and payment histories, which helps you stay on top of your financial obligations. The portal’s user-friendly interface allows for informed decision-making, enabling you to assess your loan performance effortlessly. You can as well make payments directly through the portal, streamlining your cash flow management. Automatic email notifications for new document uploads keep you updated on important changes, allowing for proactive loan management. Furthermore, access to IRS 1098 tax forms simplifies your tax preparation, reducing the time spent on administrative tasks. This combination of features not only improves your ability to manage loans effectively but likewise contributes to better overall financial health for your business. Frequently Asked Questions What Is the Mysba Loan Portal? The MySBA Loan Portal is an online platform that simplifies your management of SBA loans. It features a dashboard where you can view important loan details, such as outstanding balances and payment history. You can easily sign in or create an account using your social security number and loan number. The portal additionally allows you to make payments, access statements, and communicate with SBA representatives, ensuring you stay organized and informed about your loans. How Do Loans Help Businesses? Loans help businesses by providing vital capital for various needs, like starting operations, broadening facilities, or purchasing equipment. They enable you to manage cash flow, ensuring you can meet operational costs during market fluctuations. Furthermore, securing a loan can improve your credit profile when payments are made on time, paving the way for better financing options later. Certain loan programs offer favorable terms, making long-term financing more accessible and affordable for small businesses like yours. What Is Mysba? MySBA is a digital platform created by the Small Business Administration, focusing on managing 504 loans. It offers a user-friendly dashboard where you can view all your loans, including outstanding balances and payment history. By logging in with your social security number and SBA loan number, you can access crucial documents like IRS 1098 tax forms. The portal likewise allows direct communication with the SBA, making it easier to address any loan-related inquiries. Can Someone Help Me With My SBA Loan Login? If you’re having trouble logging into your SBA loan account, you can reach out for help. First, verify you’re using the correct credentials. If you still can’t access your account, call the customer service center at 1-833-572-0502 for assistance. They can guide you through troubleshooting steps. Conclusion In conclusion, the MySBA Loan Portal offers a thorough solution for managing SBA 504 loans, providing crucial features like direct payments and easy access to loan information. By utilizing this platform, you can improve your business’s financial management and decision-making processes. Accessing the portal is straightforward, and ample customer support is available to assist you. Overall, integrating the MySBA Loan Portal into your operations can greatly enhance your efficiency and streamline your loan management tasks. Image via Google Gemini This article, "What Is MySBA Loan Portal and How Can It Help Your Business?" was first published on Small Business Trends View the full article
-
Why TikTokers Are Injecting Salmon Sperm Into Their Faces
Scroll through TikTok or Instagram, and you'll find influencers swearing by unconventional treatments, posting dramatic before-and-after photos and glowing testimonials about their rejuvenated skin. And the skincare "It Girl" of the moment? It's salmon sperm. Yeah. As we kick off the new year—prime time for beauty resolutions!—a growing number of people are seeking out "salmon sperm facials." Before your imagination paints an extra fishy picture (pun intended), understand that people aren't really smearing straight-up salmon sperm on their face. The secret ingredient is something called PDRN, or polydeoxyribonucleotide, a compound extracted from salmon DNA. So, what exactly is this secret ingredient, and is it truly the next frontier in anti-aging skincare? The science behind the hypePDRN isn't totally snake oil; the compound has legitimate clinical backing for its regenerative properties. Research suggests that PDRN can stimulate tissue repair, promote collagen production, and improve skin elasticity by activating adenosine receptors in cells. Several sources claim it's been used in medical applications since the 1980s in Italy and South Korea. Whatever the actual origins, PDRN has gradually made its way into mainstream skincare. The treatment typically involves a series of micro-injections delivered directly into the skin, similar to mesotherapy or microneedling procedures. In the U.S., however, PDRN is only legal to use topically, since the FDA qualifies it as a beauty product and not a drug. Proponents claim it can reduce fine lines, improve skin texture, minimize scarring, and create an overall more youthful appearance. Unlike other cosmetic procedures that simply fill or temporarily plump the skin, PDRN is said to actually stimulate the skin's natural healing processes. But as always, there's a significant gap between reality and what you see online. The reality checkSocial media thrives on transformation narratives, and skincare content is no exception. The algorithms favor dramatic reveals, leading creators to emphasize stunning results while downplaying less glamorous details—like the fact that these injections can be quite painful according to some. "While PDRN has legitimate clinical data supporting skin repair and regeneration," says Dr. Claudia Kim, "viral content often exaggerates results and glosses over who is—and isn't—an appropriate candidate. Context and medical supervision matter." When it comes to the injections specifically, these treatments can cause temporary swelling and bruising. At the very least, they could require multiple sessions to see results. Again: If you're in the U.S., and there's a syringe full of salmon sperm headed straight for you, it might not be FDA-approved. That means its purity, safety, and effectiveness are not regulated. As with any medical aesthetic procedure, you shouldn't sign up for PDRN treatments without careful consideration—considerations that extend beyond the promise of better skin. Do you know which salmon DNA procedure you're signing up for? Is it an injection, or is it technically microneedling? Did you opt for PDRN or PN (polynucleotides), a purer and more concentrated form of PDRN? To make things even more confusing, these treatments can go by different names, from “salmon skin facials,” to “salmon sperm injections,” or “PDRN facials” to the brand name Rejuran. One thing is sure: As demand grows, so does the risk of unqualified practitioners offering the treatment, potentially leading to complications or disappointing results. The bottom lineThe salmon sperm trend may sound bizarre, but there is science backing it up. And when your favorite beauty influencer credits their glowing skin to a specific treatment, it's tempting to believe you can achieve the same results. Social media will always continue to drive beauty trends, and there's nothing inherently wrong with being inspired by what you see online. But for your looks and your safety, you need to understand the difference between a carefully curated social media moment and the full reality of medical aesthetic procedures. If you're intrigued by PDRN treatments after seeing them online, consult with a qualified dermatologist or licensed aesthetic practitioner. They can assess whether you're an appropriate candidate, explain realistic expectations, discuss potential side effects, and ensure the treatment is administered safely. As more advanced treatments become increasingly accessible and visible online, don't let TikTok influencers replace professional medical consultation. View the full article
-
US stocks slide after bank earnings disappoint
S&P 500 on course for worst day since mid-December as tech shares also hit View the full article
-
A quiet Google Ads setting could change your creative
Google introduced a low-visibility setting that could impact brand control for location-based ads. Driving the news. In the Shared Library under Location Manager, Google Ads now includes an option called “Google Owned Location Data.” When enabled, Google can automatically pull imagery from its own library and use it in ads tied to your business locations. Why we care. While Google frames the setting as a way to support performance goals, it allows creative assets to appear in your ads that you didn’t upload, select, or explicitly approve — a potential issue for brand-sensitive advertisers. The big picture. Automation in Google Ads continues to expand beyond bidding and targeting into creative itself. This update pushes more visual decision-making to Google, especially for advertisers running location extensions or location-based campaigns. Between the lines. For brands with strict creative guidelines, regulated industries, or franchise models, this setting could introduce inconsistencies or compliance risks without obvious alerts. What to do now. Advertisers concerned about brand control should check the Location Manager in the Shared Library and review whether Google Owned Location Data is switched on. First seen. This update was spotted by Paid Media Analyst Conor Crummey, who shared the new option he spotted on LinkedIn. The bottom line. If you value creative oversight, this is a subtle Google Ads update worth auditing — before unapproved imagery shows up in your ads. View the full article
-
Google Gemini Is About to Get to Know You Way Better
Since the days when Google Gemini was still called Bard, it's been able to connect with the company's other productivity apps to help pull context from them to answer your questions—but you still had to connect those apps to the AI manually using extensions. And even after bringing your apps together, you usually had to tell Gemini where to look for your data to get much use out of its abilities. For Instance, if you wanted it to pull information from your emails, you might have started a prompt with "Search my email." Now, Google is making it easier to connect Gemini to its various services, and adding "reasoning" when pulling context from across your Google Workspace. It's calling the feature "Personal Intelligence." Rolling out in beta for paid subscribers in the U.S. today (and coming to other countries and free users "soon"), Personal Intelligence is an opt-in feature that currently works with Gmail, Photos, YouTube, and Search, all of which you can connect in one tap while setting up the feature. That alone makes it more convenient than a collection of extensions, but there are supposedly a few upgrades to general usability as well. The biggest is that Gemini will apparently be able to "learn" about you from a grab bag of sources all at once, without you having to specify where to look, and use that information to answer your questions. Credit: Google In an example, Google has a user say "I need to replace the tires for my car. Which ones would you suggest for me?" The bot then runs through multiple reasoning steps, pulling from all the data available to it, to find out what car the prompter drives and which tires would be best for it. This can take a while, which is why there's an "Answer now" button next to the reasoning progress bar to stop the bot from getting stuck. In the example, it took about 10 seconds for the AI to generate a response. Google is promising its typical Workspace privacy guarantees with Personal Intelligence, saying "because this data already lives at Google securely, you don't have to send sensitive data elsewhere to start personalizing your experience." In other words, it's not going to move the needle on how much data about you Google can access, but at least it'll prevent you from having to connect your Workspace to third parties. Google also says, "Gemini will try to reference or explain the information it used from your connected sources so you can verify it," although we don't have any examples of that in action yet. It's worth keeping an eye out, though, if you're worried about hallucinations. To that end, the company does suggest asking Gemini for more information about what it used to come to its answers if you're unsatisfied, and to correct it "if a response feels off," perhaps by saying something like "Remember, I prefer window seats." Theoretically, Gemini will then remember this for next time, using its existing chat history feature. If you're continually unsatisfied, you can hit the thumbs down button on responses to provide feedback. How to turn on Personal Intelligence in Google GeminiGoogle says that eligible users should see an invitation to try Personal Intelligence on the Gemini home screen as soon as it's rolled out to them, but if you don't, you can turn it on manually by following these steps: Open Gemini and click or tap Settings. Click or Tap Personal Intelligence. Under Connected Apps, select which apps you would like Personal Intelligence to take information from. And that's it! Remember, Personal Intelligence is off by default and is only available for paid subscribers for now, so it may be some time until you can actually use it. Google also stresses the Gemini might not personalize every response, as that will save time on more simple requests. The company also said Personal Intelligence for AI Mode in Google Search is currently planned, but does not have a set release date. View the full article
-
interview with a conflict of interest professional
A few months ago, a commenter mentioned that they work as a conflict of interest professional, and many of us wanted to hear more. She graciously agreed to do an interview about her work, and here’s our conversation. Can you start by describing what conflict of interest professionals do, overall? So, broadly, conflict of interest professionals are usually housed somewhere in a company or university’s compliance department, working closely with the rest of the teams who make sure various laws or policies are being followed. In the most general sense, what we do is to ask questions about the non-work relationships and activities of our employees that could affect the person’s ability to do their work responsibilities, and if the responses indicate a potential issue, we work out how to mitigate the chances of the personal affecting the professional. So for example, in my prior job where I was focused on conflicts of interest related to research, you look at questions like whether a person’s outside activities affect their research. If I’m part-owner of a company and I decide to subcontract part of my university research work out to my company, or if I decide to hire my sibling to work on my research, is that an appropriate scientific decision because my company is best positioned to do the work or my sibling is the best candidate? Or is that me using the university to siphon taxpayer money for my personal use and delivering subpar work or no work at all to return something of value to the taxpayer? How can we put some oversight in place to make sure it’s the former and not the latter? In my current role I’m in a healthcare system, where the specific regulations and questions are different but the types of issues are related. So these days the questions I’m looking at look more like, if Dr. Smith has invented a new kind of knee replacement implant, and she gets royalties every time the hospital orders one, what does that mean for her clinical decisions? Are the patients aware of that, and what their alternatives are, and can they get a second opinion about whether the implant is the right one for them? Did the hospital make a decision to use this kind of implant based on her recommendation and if so did the decision maker know about her financial interest? If we look at all the doctors in the system who do this kind of surgery, does everyone use her implant at about the same rate, or is she using it four times as often as anyone else, and if so, what concerns does that raise about whether she’s making the right decisions for her patients? What are some of the challenges you run into doing this work? Perhaps obviously, this is a hard time to sell anyone on the idea that conflicts of interest, or ethical behavior in general, matter. Particularly when you are claiming that they have to do something because a federal regulation requires it. No one is looking at our current government or judicial system and saying, “Oh, yeah, that’s a federal system that cares about preventing personal interest and bias, that inspires me to be my best self and live up to both spirit and letter of the law.” Some of the other big challenges in the space are things like: • No one likes someone at work questioning them about what they do off the clock, or telling them that their off the clock activities are related to their work when they may disagree, or asking them questions about, e.g., their spouse’s salary or their sibling’s qualifications to get hired. The conversations can be really touchy, and soft skills including discretion are really important. • It’s a specialized field without much of a professional network/organization, with often only one or two people at an institution who know anything much about it, so you’re often working on your own without much of a peer group to bounce things off of or learn from. • It’s a field no one trains in; you tend to get hired because you have some transferable experience, and then learn fast on the job, but it’s not like you come in with some sort of certification ready to hit the ground running after doing a practicum and a bunch of advanced classwork. • The stakes can feel really high! On the research side, I felt that to an extent, feeling responsible for making sure that responsible, ethically conducted science was being done. But on the clinical side. I feel even more keenly that any routine decision I make on a random Tuesday can directly affect how patients’ medical care is delivered even though I’ll never be in the room with a patient. You mentioned people typically get hired for this because they have transferable experience. What kind of experience transfers well? For transferable experience, the most common path is to find someone who has some sort of compliance or regulatory experience. In my own case, I started my career as a research lab manager, doing all sorts of tasks related to running a research project, including writing and updating the compliance documents related to human subjects research ethical review. I’ve also seen people come into the field based on experience with HR work or healthcare compliance work in other areas like patient privacy or medical coding. Export compliance (dealing with shipping both physical goods and information out of country) is another common path; export and conflict-of-interest teams tend to work closely together and sometimes have some cross-training. Are there certain types of conflicts of interest that you see coming up a lot that people don’t seem to anticipate? In other words — probably most people know it’s going to get flagged if they try to hire their spouse or their kid (or maybe they don’t! tell me if they don’t because that would be fascinating too!) but are there things that seem less obvious to laypeople that they’re surprised to learn might be an issue? In the research world, the big messy thing that no one ever seemed to think enough about in advance is what happens when graduate students and their advisors start companies together based on the research they’ve done together. In the ideal world that can be really great for both of them, but when it goes bad, it can be so bad because they’re in this position where they’re co-equals at the company but then still in this very difficult power dynamic at the university, and those things can bleed over into each other and make life very difficult for them and everyone else around them. And the student may not feel at all empowered to let anyone know things have gone bad, so you really want to get ahead of that from the very beginning with someone in a position to act as an advocate for that student and check in with them regularly. How often are you having to say “no, you can’t do this” versus “you can do this but we have to do XYZ to mitigate the chances of it affecting things inappropriately”? In my old research world, a “no” was extraordinarily rare; the university was extremely motivated to support research and entrepreneurship and to find ways to mitigate when the two got entangled in messy ways. I would find myself saying a flat no maybe once a year or so, and only to the most clear-cut things. (For example: The guy who thought he could use about six figures of university discretionary funds to just buy really expensive equipment for his company because his company didn’t have the cash flow handy.) In my current clinical role, there are more things that are just a clear-cut policy no. Mostly things that edge up toward the appearance of being paid by, e.g., pharmaceutical companies to promote products. Both morally and legally, we just can’t have our patients left wondering whether they’re getting prescribed a medication because it’s the best one for them or because their doctor is getting wined and dined by the pharma company. Do people ever throw tantrums about this or do people generally get it? 95% of people genuinely want to do the right thing but just don’t know what problems could arise or what the policies are, and when you tell them, they will do the right thing even if they grumble a little about the red tape. And then the other small handful do in fact throw temper tantrums, try to get their department chair to exempt them, complain that the questions are none of their workplace’s business, etc. I assume that handful of people exists in every field and job! I published a letter once from someone whose husband didn’t want to comply with her company’s stock trading policies and didn’t think he should have to since he himself wasn’t their employee. Do you run into issues with spouses balking like that? Yes! This doesn’t happen often. But it does happen, and I had one just recently. I worked with my leadership to talk over the person’s spouse’s concerns and we decided that for the time being, it was sufficient for the employee to confirm to us that he had reviewed his spouse’s interests and that none of them were in companies closely related to the clinical care this person provides. We did make it clear that at some point in the future we may need to revisit that decision. Another option I could use in a case like this is, sometimes the person doesn’t want that information in a database but is willing to tell one person. So they might tell me, or their department chair, and that person then does some due diligence outside the standard process so the final record only shows that a review was done and no issues discovered. (And that’s part of the soft skills stuff — I have to have built up enough trust and credibility that if I make that offer, they believe me!) Realistically, do internal politics ever affect the outcome when you flag a conflict? Do you see people getting away with conflicts because they have a lot of capital within the organization or are there effective safeguards against that? You never want that to happen but it can. A university might be willing to make an exception with a $5 million grant on the line that they wouldn’t make with a $50,000 grant on the line, especially in the current scientific funding climate. Or a clinician who was a big-deal hire for a hospital might have negotiated as part of their hire some favorable terms related to outside work beyond what the policies typically permit. I do what I can to mitigate and document and make sure everyone who could be affected is aware that this is being handled differently than typical and that it’s not meant to serve as precedent. And then I brace to have to explain to five other people who have heard a rumor that X policy has changed, that it has not actually changed. I’m super interested in the detective work you mentioned (figuring out what people didn’t tell you). When you uncover things that way, does it generally turn out to be an innocent mistake (they genuinely didn’t think about X or didn’t realize they needed to disclose X) or are you also finding some people are deliberately not forthcoming? It’s almost always innocent — people just forget about some one-off consulting they did 11 months ago when it’s time for annual disclosure, or forgot to add something, or didn’t realize that something needed to be disclosed. I have run into situations where someone was not being forthcoming but in those cases it’s never really been about the conflict of interest itself. There’s typically some other larger issue of bad-faith conduct going on and at some point someone says “hey, we should also check the conflict of interest records.” It becomes one piece in a bigger pattern of problem behavior and I rarely get to know the whole story. I’m also interested in the soft skills involved in having potentially touchy conversations with people about this stuff. What are some of the secrets to doing that well? The soft skills piece is tricky for me because my natural tendency can be too lean too far in the direction of smoothing ruffled feathers and being a people pleaser. So, soft skills — but with a firm boundary somewhere underneath them. It’s a hard balance! One thing I learned from watching a mentor years ago is that since I’m almost always talking with professors and/or clinicians who are rightfully really proud of their work and expertise, it can help set the right tone if I start off by asking them to tell me about their research or their company generally before we get into the specifics of whatever we’re meeting about. Once in a while it leads me to some useful tidbit, more often it just gives them a chance to tell me about the thing they’re proud of, and I get to tell them how cool and interesting it is, maybe ask a couple of questions — because it often really is interesting and cool! It’s usually five minutes of a meeting that doesn’t actually affect the outcome but sets a positive tone and lets me display that I’m interested in their work and not just in being a policy robot. Beyond that, it helps to keep in mind, and sometimes to actually tell them out loud, that I’m not looking to say no — I’m always hoping to find a way to get to a version of “yes” that lets them do the work they want to do while protecting them, the institution, their discoveries, and their patients. I also make an extra effort to get to know, and be in the good graces of, department chairs and administrative coordinators — they know everything and are vital allies. And if a professor has been an unusual pleasure to work with I make sure to mention that to the chair/administrator as well. They so often only hear complaints from people in my type of role that I try to be the voice of good news when I can, not only problems. Can you share a particularly ridiculous/outrageous conflict you uncovered and how it was handled? I think I can say broadly that the most ridiculous ones almost always ended up being the ones involving family. With the financial ones and even the student/teacher ones, there’s a reasonably clear way to point out to people that objectively, doing X appears to create financial benefit Y for their company, or that if they and their student have a disagreement at their joint company, it can create problems at the university. But the family relationships seem to touch a whole different nerve, maybe because it sounds like you’re telling someone you know more about how their relationships work than they do. So if I tell someone that I cannot approve them being the person who signs off on their mother-in-law’s work and approves the size and timing of their mother-in-law’s paycheck, that somehow gets a lot more upsetting to them. Because if they tell me that they and their mother-in-law are absolutely 100% capable of keeping things professional, and I try to explain that I’m sure that’s true for them but it’s not true for everyone and I can’t take on the role of evaluating each person’s personal relationships with their in-laws so we have to build the policies around something else, that starts to feel really personal. (It was only a mother-in-law once. Usually spouses or partners, occasionally siblings or parents, rarely grown children. The mother-in-law was absolutely the worst. That person offered to have their spouse call and tell me how good the family relationships were and that it would not be a problem. In the end, their department chair had to help lay the law down that we needed a second set of eyes on the payment process. I lived in fear for the five years of that grant that the professor was going to get a divorce and blow up the family and the grant.) The post interview with a conflict of interest professional appeared first on Ask a Manager. View the full article
-
US evacuates personnel from Qatar military base as Trump threatens Iran
Move comes amid growing concern American action against Tehran could destabilise regionView the full article
-
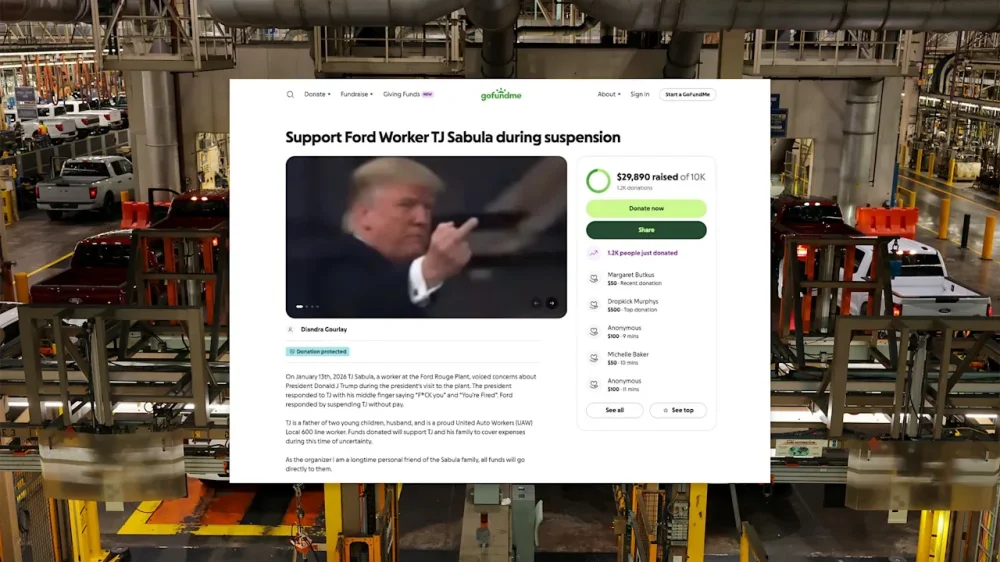
GoFundMe campaign for Ford worker TJ Sabula quickly tops $90K in latest politically charged fundraiser
A GoFundMe page is raising thousands to support a worker at the Ford Rouge Plant in Dearborn, Michigan, after he openly criticized President The President—to his face. The worker, identified in media reports as TJ Sabula, heckled The President while he was visiting the plant on January 13. In a video obtained by TMZ, Sabula can be heard calling the president a “pedophile protector.” In response, the president can be seen mouthing an expletive and telling Sabula “you’re fired” before flipping him off. Ford reportedly didn’t hesitate to act, with the automotive giant immediately suspending Sabula, according to the Wall Street Journal. Fast Company reached out to Ford for comment. Predictably, and almost just as fast, a GoFundMe page was launched in support of Sabula. “TJ is a father of two young children, husband, and is a proud United Auto Workers (UAW) Local 600 line worker,” the page reads. “Funds donated will support TJ and his family to cover expenses during this time of uncertainty.” At present, the fundraising page, which has only been live for about 11 hours, has raised more than $90,000. Given that GoFundMe and other crowdfunding platforms are increasingly relied upon to help people going through financial challenges—sometimes spurred by political events—it’s not the first time the site has made headlines recently. Less than a week ago, after 37-year-old Renee Good was shot by an ICE agent in her neighborhood, a fundraiser was launched to support her family. The page has amassed over $1.5 million. Additionally, a page for Jonathan Ross, the ICE agent who shot and killed Good, was also created. That page has raised $700,000 at present, including a $10,000 donation from billionaire Bill Ackman. Fast Company has reached out to GoFundMe to ask if it has verified the campaign for Sabula. Engine troubles Sabula’s suspension is not terribly surprising. While Ford Motor CEO Jim Farley and the president have had a complicated relationship at times, Farley has also expressed optimism about The President’s second term. He joined President The President in December when he announced a proposal to slash Biden-era fuel economy standards. Ford also donated $1 million in cash and a fleet of vehicles to the president’s January 2025 inauguration. Following his suspension, Sabula told The Washington Post that he has “no regrets whatsoever” about heckling the president. He added that The President was only standing about 60 feet away and heard him “very, very, very clearly.” View the full article
-
How to do an in-depth portfolio review with these 8 steps
If you’d like to do a thorough review of your portfolio and plan, here are the key steps to take. I recommend doing them over a series of sessions, not all at once. Step 1: Gather your documentation This could be your current investment statements, plus Social Security and pension. Pro tip: Set up a My Social Security account to get an overview of your benefits and earnings history. Step 2: Ask and answer: How am I doing? To find out if you’re on track to reach your financial goals, review your current portfolio balance, combined with your savings rate. Tally your contributions across all accounts. A decent baseline savings rate is 15%, but higher-income folks will want to aim for 20% or more. Also factor in other goals you’d like to achieve, such as college funding or a home down payment. Are they realistic? Make sure you’re not giving short shrift to retirement. If you’re retired or about to be, the key gauge of the viability of your total plan is your withdrawal rate—your planned portfolio withdrawals divided by your total portfolio balance. The 4% guideline is a good starting point, but aim for less if you can. Step 3: Check up on your long-term asset allocation Does your total portfolio’s mix of stocks, bonds, and cash match your targets? High-quality target-date series such as those from Vanguard and BlackRock’s LifePath Index Series can help benchmark asset allocation. My model portfolios can also help. A portfolio that tilts mostly or even entirely toward stocks makes sense for younger investors. If your portfolio is notably equity-heavy and you’re within 10 years of retirement, shifting to bonds and cash is more urgent. Just mind the tax consequences when you rebalance. Step 4: Assess liquid reserves Holding some cash is crucial to ensure you don’t have to tap your investments or resort to credit cards in a financial crunch. For retired people, I recommend holding six months to two years worth of portfolio withdrawals in cash investments. For those still working, holding three to six months’ worth of living expenses in cash is a good starting point. Step 5: Assess suballocations, sector positioning, and holdings Your broad asset-class exposure largely determines how your portfolio behaves. But your positioning within each asset class also deserves a look. Market strength has recently broadened, but growth stocks and funds that own them have outpaced value by a wide margin over the past decade. Finally, check up on your sector positioning, allocation to foreign stocks, and actual holdings. Step 6: Identify opportunities to streamline Why have scores of accounts and holdings if a more compact portfolio could do the job just as well? If you’ve changed jobs, you may have multiple 401(k)s and rollover IRAs. Consider consolidating into a single IRA. If you have several small cash accounts, you may be losing out on a (slightly) higher yield. Could you reduce the number of holdings in your portfolios? Index funds and ETFs provide pure asset-class exposure and a lot of diversification in a single package. I also like target-date funds for smaller accounts to provide diversification without any maintenance obligations. Step 7: Manage for tax efficiency At this point, if you think changes are in order, be sure to take tax and transaction costs into account. Focus any selling in your tax-sheltered accounts, where you won’t incur tax costs and you can usually avoid transaction costs, too. Within your taxable accounts, review the tax implications and/or get tax advice before executing trades. Also review whether you’re managing your portfolio with an eye toward tax efficiency. Are you making contributions to your tax-sheltered vehicles? Are your taxable accounts as tax-efficient as possible? For a lot of people, this is as simple as holding equity ETFs and/or municipal bonds and bond funds for their taxable accounts. Finally, think about tax-efficient withdrawal sequencing. Step 8: Troubleshoot other risk factors Uninsured long-term-care risk is a significant factor for those who are neither well off nor eligible for Medicaid. Develop a plan in case you have sizable long-term-care outlays later in life. Another common risk factor is providing help to loved ones. In this case, it’s often helpful to talk to a financial advisor and/or estate planner to figure out how you can help without jeopardizing your financial future. This article was provided to The Associated Press by Morningstar. For more personal finance content, go to https://www.morningstar.com/personal-finance. Christine Benz is director of personal finance and retirement planning for Morningstar. Related Links 5 Smart Ways to Diversify Your Portfolio for 2026 https://www.morningstar.com/portfolios/5-smart-ways-diversify-your-portfolio-2026 8 Reasons You Might Need to Tweak Your Portfolio https://www.morningstar.com/portfolios/8-reasons-you-might-need-tweak-your-portfolio An Investing Guide for Every Life Stage https://www.morningstar.com/personal-finance/an-investing-guide-every-life-stage —Christine Benz of Morningstar View the full article
-
UK borrowing costs fall to lowest in more than a year
Rate cut bets and easing tensions over government borrowing fuel gilts rallyView the full article
-
5 Profitable Local Franchises to Consider
If you’re exploring profitable local franchise opportunities, several options stand out in today’s market. Techy specializes in gadget repairs, catering to the increasing demand for sustainable solutions. Blaze Pizza offers a customizable dining experience with rapid expansion potential. Other notable franchises include Right at Home for senior care, Fitness Together for personalized training, and Smoothie Factory for health-focused offerings. Each franchise presents unique business models that can lead to success, but which one aligns best with your goals? Key Takeaways Techy Franchise offers a growing demand for gadget repair services, focusing on sustainability and recurring revenue streams. Blaze Pizza’s unique build-your-own model and extensive support make it a solid investment in the fast-casual dining sector. Right at Home taps into the booming senior care market, providing essential services to an aging population with projected growth. Fitness Together emphasizes personalized training, fostering community engagement, and boasts low failure rates, ensuring profitability for franchisees. Smoothie Factory capitalizes on the health trend with high-profit margins and low overhead costs, appealing to health-conscious consumers. Techy Franchise: Best for Parts, Accessories, and Gadget Repair In today’s tech-driven world, the demand for gadget repair services is on the rise, making tech franchises an attractive business opportunity for aspiring entrepreneurs. Local franchises specializing in parts, accessories, and gadget repair offer established business models that simplify operations. This means you can focus more on customer service and satisfaction rather than starting from scratch. With consumers increasingly opting for repairs over replacements, you can tap into a growing market that values sustainability. Many tech franchises additionally provide recurring revenue streams through maintenance contracts and service plans, ensuring stability in your earnings. Although some franchises can be costly, options like CMIT Solutions offer entry costs starting around $106,450, making it a viable choice for those seeking a free franchise opportunity. Blaze Pizza: Best Franchise Opportunity With over 400 locations, Blaze Pizza stands out as a leading franchise opportunity in the fast-casual dining sector. Founded in 2011, it’s gained recognition for its unique build-your-own pizza model, allowing customers to customize their pizzas with fresh ingredients. This approach promotes a loyal customer base, driving repeat business. The initial investment to open a franchise ranges from $500,000 to $800,000, which includes a $30,000 franchise fee. Franchisees benefit from extensive training programs and ongoing support, ensuring they adhere to a proven operational model. Blaze Pizza has been recognized as one of the fastest-growing restaurant chains in America, highlighting its strong market presence and innovative approach to dining that emphasizes high-quality ingredients and customer satisfaction. Right at Home: Best for Senior Care Right at Home stands out as a premier choice for those interested in the senior care franchise sector, especially considering the growing need for in-home care services. With the senior population projected to reach 70 million by 2030, the demand for thorough care is increasing. Operating over 300 locations in the U.S. and internationally, Right at Home boasts strong brand recognition and extensive reach. Their services, including personal care, companionship, and assistance with daily living activities, cater to families seeking support for elderly loved ones. The senior care market is expected to double in value, reaching approximately $141 billion by 2033. Franchisees receive continuous support and resources, ensuring they’re well-equipped to provide high-quality care. Fitness Together: Best Gym Franchise Fitness Together stands out as a leading choice for those interested in the gym franchise industry, primarily due to its unique focus on personalized training. This franchise model emphasizes one-on-one sessions, tailoring fitness plans to meet individual client needs and goals. With over 200 locations across the United States as of 2023, Fitness Together has proven its effectiveness and popularity in the fitness market. The franchise likewise promotes community engagement, creating a supportive atmosphere that improves member retention and satisfaction. In addition, Fitness Together provides thorough training and ongoing support for franchisees, equipping you to operate successfully. Its established business model boasts a strong track record of profitability and low failure rates, making it an appealing option for aspiring entrepreneurs. Smoothie Factory: Best Franchise for Health Care As the health and wellness movement continues to gain momentum, Smoothie Factory emerges as a top choice for entrepreneurs looking to invest in a health-focused franchise. This franchise offers a variety of smoothies, juices, and healthy snacks, catering to the rising demand for nutritious food options. With over 30 years of experience, Smoothie Factory boasts a proven business model emphasizing quality ingredients and customer satisfaction. An initial investment starts around $150,000, allowing for low overhead costs and high-profit margins because of affordable ingredients. Franchisees benefit from extensive support, including training and marketing assistance. As the global health food market is projected to reach $1 trillion by 2027, joining Smoothie Factory positions you for substantial growth opportunities. Frequently Asked Questions What Franchise Is the Most Profitable to Own? When considering which franchise is the most profitable to own, you should evaluate various sectors. Quick-service restaurants typically offer strong profit margins of 4-6% and gross margins around 65-70%. The fitness industry is likewise booming, with revenue expected to double in the coming years. Senior care franchises are gaining traction because of their recession resistance. Finally, cleaning services present low startup costs and high recurring revenue, making them attractive options for prospective franchisees. What Is the 7 Day Rule for Franchise? The 7 Day Rule for franchises requires franchisors to provide you with a Franchise Disclosure Document (FDD) at least seven days before you sign any agreement or make payments. This rule, mandated by the Federal Trade Commission (FTC), guarantees you have time to review important details, like fees, obligations, and the franchisor’s financial performance. Adhering to this rule is vital for franchisors, as non-compliance can lead to legal issues and potential rescission of agreements. What Is the Cheapest Most Profitable Franchise to Own? The cheapest, most profitable franchise to own often includes service-based options like mobile pet grooming or cleaning services, which can start under $50,000. Fast-casual food franchises, such as coffee shops, additionally provide a solid return, with investments typically between $50,000 and $100,000. Education franchises in tutoring can be affordable too, often around $30,000, capitalizing on growing demand. These franchises usually come with strong support systems that help guarantee success and profitability. Why Is It Only $10,000 to Open a Chick-Fil-A? It’s only $10,000 to open a Chick-fil-A since the company covers most startup costs like equipment, real estate, and construction. This low initial investment is attractive, especially since franchisees pay a 15% royalty fee on sales, which is higher than many competitors. Nevertheless, Chick-fil-A’s selective franchisee process guarantees you possess strong leadership skills and commitment, requiring you to be hands-on in operations for at least 40 hours a week to secure success. Conclusion In conclusion, exploring these five profitable local franchises—Techy, Blaze Pizza, Right at Home, Fitness Together, and Smoothie Factory—can lead to successful business opportunities. Each franchise caters to specific market demands, from technology repair to health food, ensuring a diverse range of options. By comprehending their unique business models and support systems, you can make an informed decision that aligns with your interests and financial goals, in the end positioning yourself for growth in a competitive market. Image via Google Gemini This article, "5 Profitable Local Franchises to Consider" was first published on Small Business Trends View the full article
-
5 Profitable Local Franchises to Consider
If you’re exploring profitable local franchise opportunities, several options stand out in today’s market. Techy specializes in gadget repairs, catering to the increasing demand for sustainable solutions. Blaze Pizza offers a customizable dining experience with rapid expansion potential. Other notable franchises include Right at Home for senior care, Fitness Together for personalized training, and Smoothie Factory for health-focused offerings. Each franchise presents unique business models that can lead to success, but which one aligns best with your goals? Key Takeaways Techy Franchise offers a growing demand for gadget repair services, focusing on sustainability and recurring revenue streams. Blaze Pizza’s unique build-your-own model and extensive support make it a solid investment in the fast-casual dining sector. Right at Home taps into the booming senior care market, providing essential services to an aging population with projected growth. Fitness Together emphasizes personalized training, fostering community engagement, and boasts low failure rates, ensuring profitability for franchisees. Smoothie Factory capitalizes on the health trend with high-profit margins and low overhead costs, appealing to health-conscious consumers. Techy Franchise: Best for Parts, Accessories, and Gadget Repair In today’s tech-driven world, the demand for gadget repair services is on the rise, making tech franchises an attractive business opportunity for aspiring entrepreneurs. Local franchises specializing in parts, accessories, and gadget repair offer established business models that simplify operations. This means you can focus more on customer service and satisfaction rather than starting from scratch. With consumers increasingly opting for repairs over replacements, you can tap into a growing market that values sustainability. Many tech franchises additionally provide recurring revenue streams through maintenance contracts and service plans, ensuring stability in your earnings. Although some franchises can be costly, options like CMIT Solutions offer entry costs starting around $106,450, making it a viable choice for those seeking a free franchise opportunity. Blaze Pizza: Best Franchise Opportunity With over 400 locations, Blaze Pizza stands out as a leading franchise opportunity in the fast-casual dining sector. Founded in 2011, it’s gained recognition for its unique build-your-own pizza model, allowing customers to customize their pizzas with fresh ingredients. This approach promotes a loyal customer base, driving repeat business. The initial investment to open a franchise ranges from $500,000 to $800,000, which includes a $30,000 franchise fee. Franchisees benefit from extensive training programs and ongoing support, ensuring they adhere to a proven operational model. Blaze Pizza has been recognized as one of the fastest-growing restaurant chains in America, highlighting its strong market presence and innovative approach to dining that emphasizes high-quality ingredients and customer satisfaction. Right at Home: Best for Senior Care Right at Home stands out as a premier choice for those interested in the senior care franchise sector, especially considering the growing need for in-home care services. With the senior population projected to reach 70 million by 2030, the demand for thorough care is increasing. Operating over 300 locations in the U.S. and internationally, Right at Home boasts strong brand recognition and extensive reach. Their services, including personal care, companionship, and assistance with daily living activities, cater to families seeking support for elderly loved ones. The senior care market is expected to double in value, reaching approximately $141 billion by 2033. Franchisees receive continuous support and resources, ensuring they’re well-equipped to provide high-quality care. Fitness Together: Best Gym Franchise Fitness Together stands out as a leading choice for those interested in the gym franchise industry, primarily due to its unique focus on personalized training. This franchise model emphasizes one-on-one sessions, tailoring fitness plans to meet individual client needs and goals. With over 200 locations across the United States as of 2023, Fitness Together has proven its effectiveness and popularity in the fitness market. The franchise likewise promotes community engagement, creating a supportive atmosphere that improves member retention and satisfaction. In addition, Fitness Together provides thorough training and ongoing support for franchisees, equipping you to operate successfully. Its established business model boasts a strong track record of profitability and low failure rates, making it an appealing option for aspiring entrepreneurs. Smoothie Factory: Best Franchise for Health Care As the health and wellness movement continues to gain momentum, Smoothie Factory emerges as a top choice for entrepreneurs looking to invest in a health-focused franchise. This franchise offers a variety of smoothies, juices, and healthy snacks, catering to the rising demand for nutritious food options. With over 30 years of experience, Smoothie Factory boasts a proven business model emphasizing quality ingredients and customer satisfaction. An initial investment starts around $150,000, allowing for low overhead costs and high-profit margins because of affordable ingredients. Franchisees benefit from extensive support, including training and marketing assistance. As the global health food market is projected to reach $1 trillion by 2027, joining Smoothie Factory positions you for substantial growth opportunities. Frequently Asked Questions What Franchise Is the Most Profitable to Own? When considering which franchise is the most profitable to own, you should evaluate various sectors. Quick-service restaurants typically offer strong profit margins of 4-6% and gross margins around 65-70%. The fitness industry is likewise booming, with revenue expected to double in the coming years. Senior care franchises are gaining traction because of their recession resistance. Finally, cleaning services present low startup costs and high recurring revenue, making them attractive options for prospective franchisees. What Is the 7 Day Rule for Franchise? The 7 Day Rule for franchises requires franchisors to provide you with a Franchise Disclosure Document (FDD) at least seven days before you sign any agreement or make payments. This rule, mandated by the Federal Trade Commission (FTC), guarantees you have time to review important details, like fees, obligations, and the franchisor’s financial performance. Adhering to this rule is vital for franchisors, as non-compliance can lead to legal issues and potential rescission of agreements. What Is the Cheapest Most Profitable Franchise to Own? The cheapest, most profitable franchise to own often includes service-based options like mobile pet grooming or cleaning services, which can start under $50,000. Fast-casual food franchises, such as coffee shops, additionally provide a solid return, with investments typically between $50,000 and $100,000. Education franchises in tutoring can be affordable too, often around $30,000, capitalizing on growing demand. These franchises usually come with strong support systems that help guarantee success and profitability. Why Is It Only $10,000 to Open a Chick-Fil-A? It’s only $10,000 to open a Chick-fil-A since the company covers most startup costs like equipment, real estate, and construction. This low initial investment is attractive, especially since franchisees pay a 15% royalty fee on sales, which is higher than many competitors. Nevertheless, Chick-fil-A’s selective franchisee process guarantees you possess strong leadership skills and commitment, requiring you to be hands-on in operations for at least 40 hours a week to secure success. Conclusion In conclusion, exploring these five profitable local franchises—Techy, Blaze Pizza, Right at Home, Fitness Together, and Smoothie Factory—can lead to successful business opportunities. Each franchise caters to specific market demands, from technology repair to health food, ensuring a diverse range of options. By comprehending their unique business models and support systems, you can make an informed decision that aligns with your interests and financial goals, in the end positioning yourself for growth in a competitive market. Image via Google Gemini This article, "5 Profitable Local Franchises to Consider" was first published on Small Business Trends View the full article
-
Denmark boosts military presence on Greenland
Meeting with senior US figures follows escalating Donald The President campaign to take GreenlandView the full article
-
Workday’s New Conversational ATS Streamlines Frontline Hiring Process
In a rapidly changing labor market, speed and simplicity in hiring can differentiate successful businesses from their competitors. Workday is addressing this need directly with the launch of its new Paradox Conversational Applicant Tracking System (ATS), now available for organizations that hire frontline workers. This innovative tool leverages artificial intelligence to streamline the hiring process, transforming how small businesses approach staffing. Workday, recognized for its enterprise AI platform, is set to enhance the recruitment experience with the Paradox Conversational ATS. By replacing lengthy application forms and complex logins with a straightforward chat-like interface, businesses can significantly reduce the friction traditionally associated with applying for frontline roles. Aashna Kircher, Workday’s group general manager for the office of the CHRO, emphasized the solution’s potential: “Paradox Conversational ATS removes that friction by helping to streamline up to 90% of hiring tasks and letting candidates apply in minutes via their phone.” The system is particularly aimed at industries with high-volume hiring needs, such as retail and hospitality. These sectors often face hurdles with traditional recruitment methods, which can alienate potential candidates who are busy or less tech-savvy. With the new ATS, candidates can inquire about job openings, submit applications, and even undergo interviews through natural, text-based conversations—often concluding the entire process within just a few days. Proven benefits for small businesses include the ability to attract more applicants quickly. Organizations utilizing this ATS note an impressive 72% average application completion rate, as candidates engage with a two-minute chat. Additionally, Workday reports that this tool minimizes administrative burdens by automating screening and scheduling functions, transforming tasks that used to take hours into mere minutes. One of the standout features of the Paradox ATS is its efficiency in the hiring cycle. Businesses using this system currently experience an average time-to-hire of just three and a half days, a significant reduction compared to traditional methods. Moreover, candidates report a 95% satisfaction rating during onboarding due to automatic delivery of offers and documentation via text, enhancing the overall experience. While the advantages are clear, small business owners should also be mindful of potential challenges. Transitioning to an automated system requires an initial investment in training and technology; not all staff may be comfortable with a tech-driven approach at first. Additionally, businesses must ensure they maintain a personal touch throughout the recruiting experience—something crucial in frontline roles where employee engagement is particularly important. For smaller organizations that rely heavily on frontline workers, the Paradox Conversational ATS presents a compelling case for improvement. Not only does it relieve the administrative backlog often experienced in high-volume hiring, but it also allows small businesses to focus on candidate experience, which can lead to better retention in the long run. As part of a holistic workforce management strategy, the Paradox Conversational ATS works alongside other tools in Workday’s suite, such as the forthcoming Workday Frontline Agent, set to launch in Spring 2026. This complementary system will help managers oversee time, absences, and scheduling changes through simple text interactions, aiming to cut down management time spent by up to 90%. Given the pressing need for innovative solutions in recruitment, especially in high-demand industries, the Paradox Conversational ATS could mark a turning point for small businesses. The ability to hire faster while ensuring a positive candidate experience can lead to not just immediate gains but sustainable success in attracting and retaining talent. Organizations interested in leveraging this AI-driven solution can learn more about its availability and features by visiting Workday’s official page. With the right tools, small businesses can not only keep pace with industry demands but also position themselves as employers of choice in a competitive marketplace. Image via Google Gemini This article, "Workday’s New Conversational ATS Streamlines Frontline Hiring Process" was first published on Small Business Trends View the full article